





How many of you have ever forgotten a password?
How many of you have ever used the same password for multiple accounts?
How many of you have ever got a phishing email?
Any idea, suggestions what "Passwordless Authentication" could be?
81% Hacking-related breaches are caused by weak or stolen passwords
Verizon Data Breach Report
1,265% Rise in malicious phishing emails since Q4 2022
SlashNext 2023 State of Phishing Report
Common Attack Vectors:
User Behaviors:
Organization Costs:
Policy Challenges:
Common Pain Points:
Had you ever had a complex password policy / complicated authentication process?
Password Managers:
Multi-Factor Authentication:
authentication without a password or any other knowledge-based secret
relying instead on ownership (e.g. devices)
or inherence (e.g., biometrics) factors
Have you ever used Passwordless Authentication?
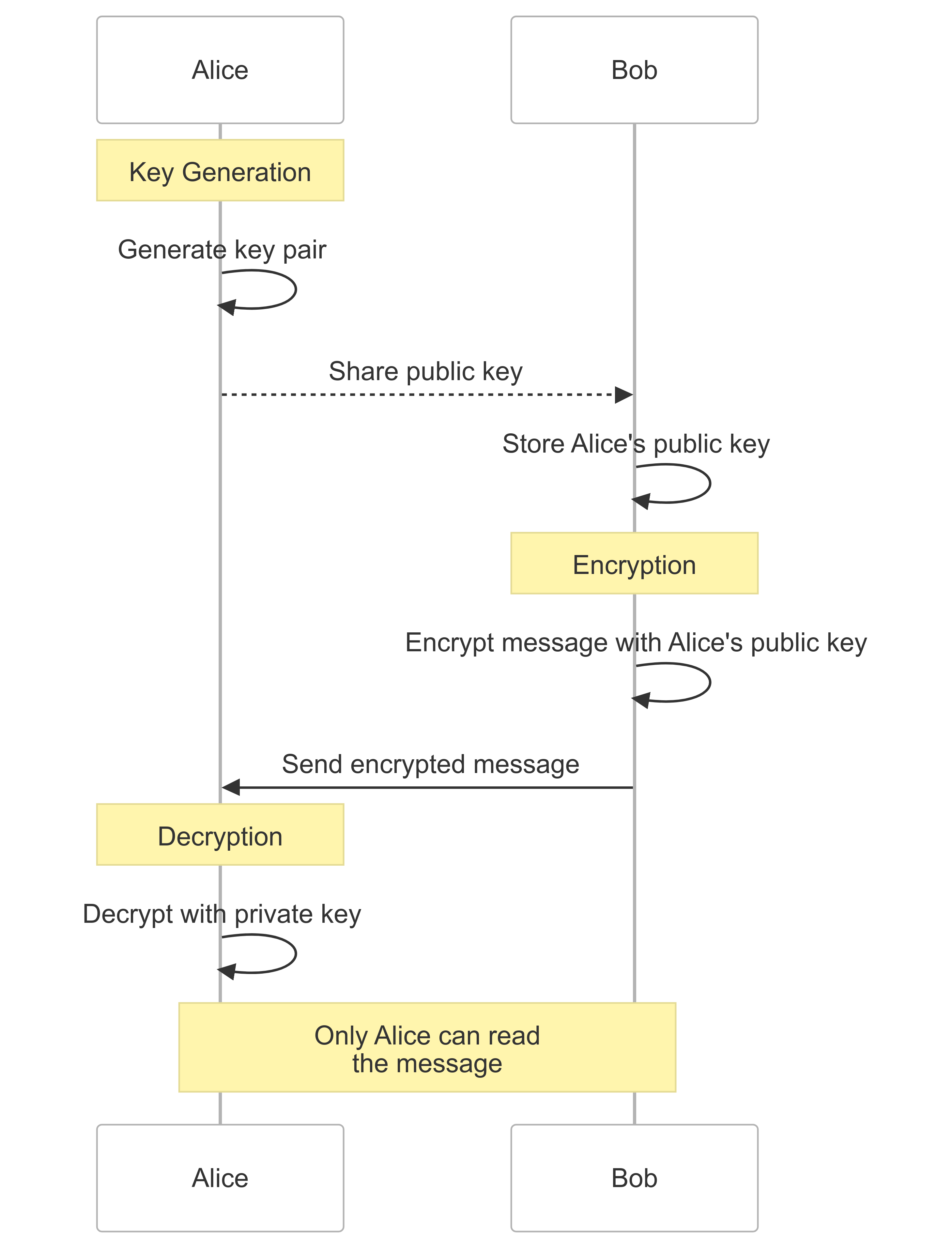
Core Concept: A system using pairs of keys:
Primary Uses:
Key Properties:
Major Backers:
Advantages:
Compatibility:
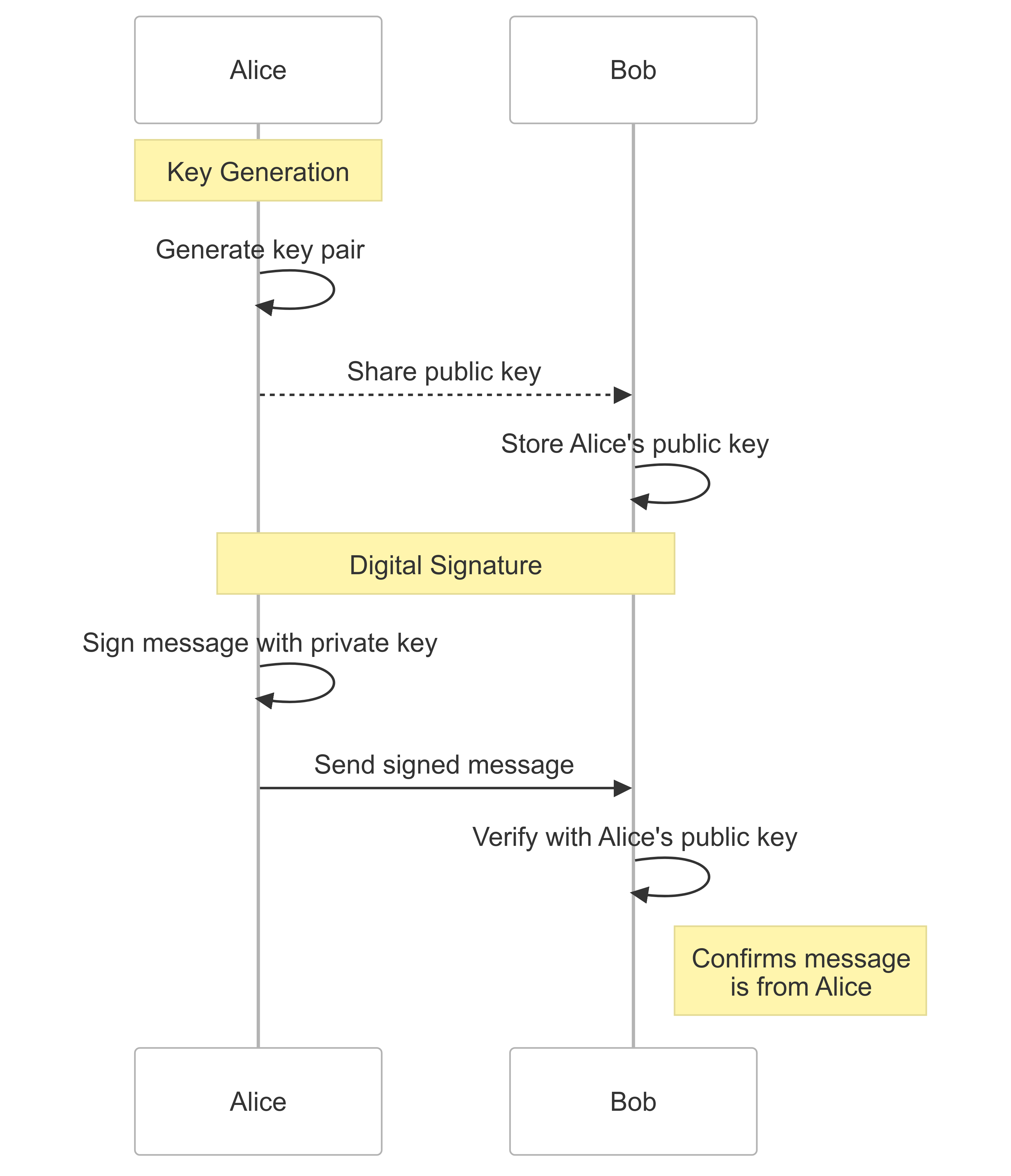
What are Passkeys?
A easy, user friendly, system-level integration of FIDO2 standard
Core Components:
Features
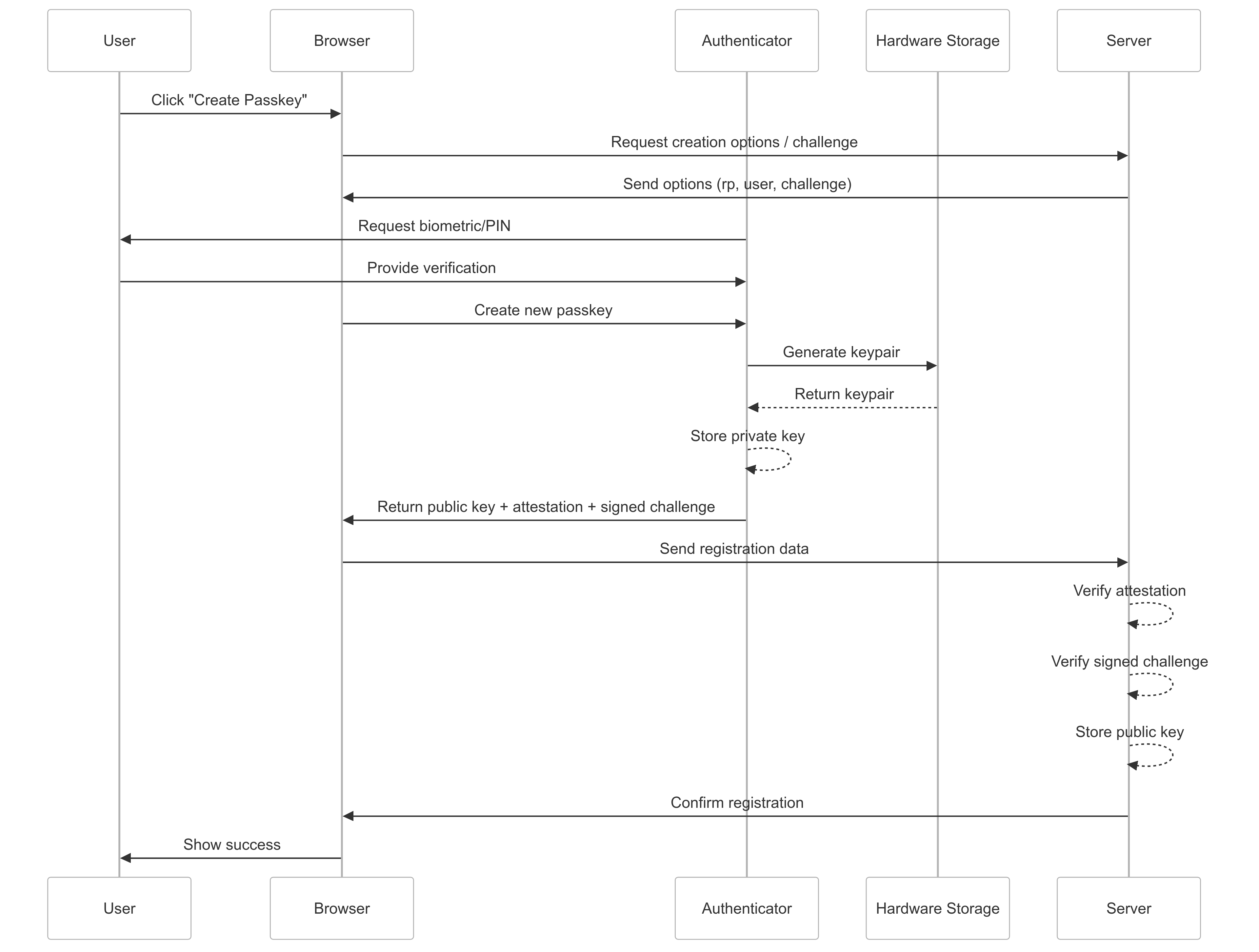
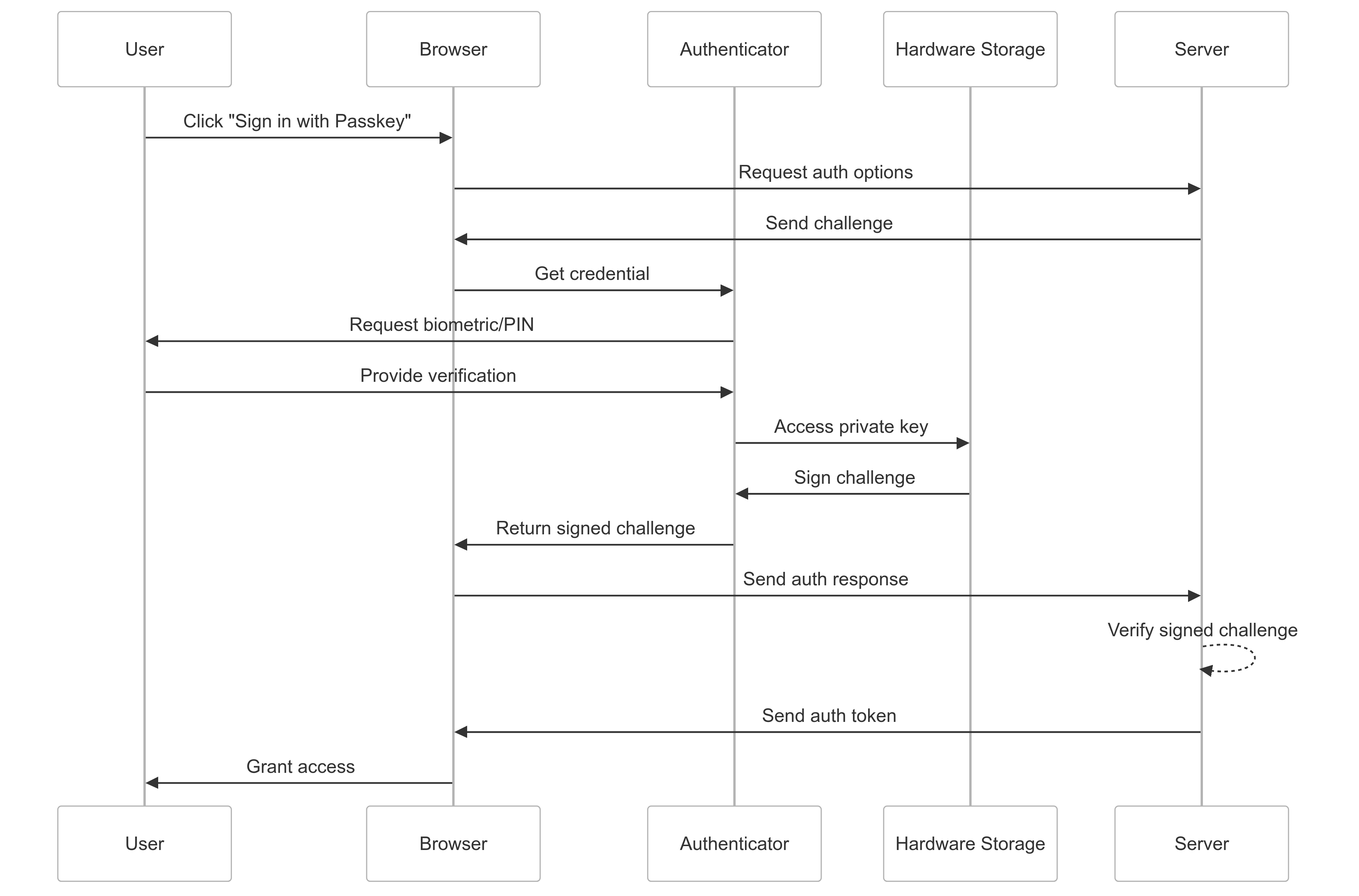
Let's examine how these work together...
| Attack Vector | How Passkeys Mitigate |
|---|---|
| Phishing | no shared secrets + Domain binding |
| Brute Force | cryptographic keys not guessable |
| Database Breaches | no shared secrest - Server only stores public keys |
| Credential Stuffing | unique key pairs per site/account |
| Social Engineering | no secrets to steal + device bound |
| Man-in-the-Middle | challenge-response + domain verification prevents replay |
| Password Spraying | no common passkeys |
Streamlined Authentication Processes:
Enhanced Usability for Employees:
Standardization Across Devices:
Lower IT Support Costs:
Reduced Compliance Costs:
Usability and User Resistance
Technical and Infrastructure Barriers
Cost and Compliance Concerns
Key Benefits
Transition Strategies
| MFAs | Passwordless | |
|---|---|---|
| Security | additional Security, but still vulnerable to phishing | not vulnerable to phishing, secured by biometric data or device security |
| UX | additional steps and setup needed, still more secure than passwords | easier to use and faster usage |
| Availability | not always available, depends on the service | more and more services offer passwordless authentication but still fairly new |
What happens when something goes wrong? f.e. lost device, broken device, etc.
No recovery solution proposed by FIDO2 Standard
Several options:
some solutions reduce the security of passkeys